¿Has sido víctima de un ciberataque?
Cada vez son más las empresas que están siendo víctimas de ciberataques. La tecnología es esencial en prácticamente todos los negocios, por lo que nos obliga a tener un mayor control de lo que entra y sale de nuestra red, ya sea malicioso o no. Los ciberataques están a la orden del día y pueden darse de diferentes formas, desde robos de información para su posterior venta en la deep web hasta la interrupción de la producción de las empresas.
Las pymes se han convertido en uno de los blancos preferidos de los ciberdelincuentes debido a sus pocos recursos en ciberseguridad, las consecuencias de estos ataques tienen un coste bastante elevado que la mayoría de estas empresas no puede afrontar y acaba cerrando (Link). En este artículo comentamos los pasos a seguir si has sido víctima de un ciberataque y expondremos de forma resumida la hoja de ruta que requiere una situación de este tipo.
Cómo actuar ante un ciberataque
Lo primero que tenemos que tener en cuenta es que ningún elemento conectado a la red tiene la posibilidad de ser 100% seguro, pero sí que podemos esforzarnos en dificultar todo lo posible la actividad de los ciberdelincuentes.
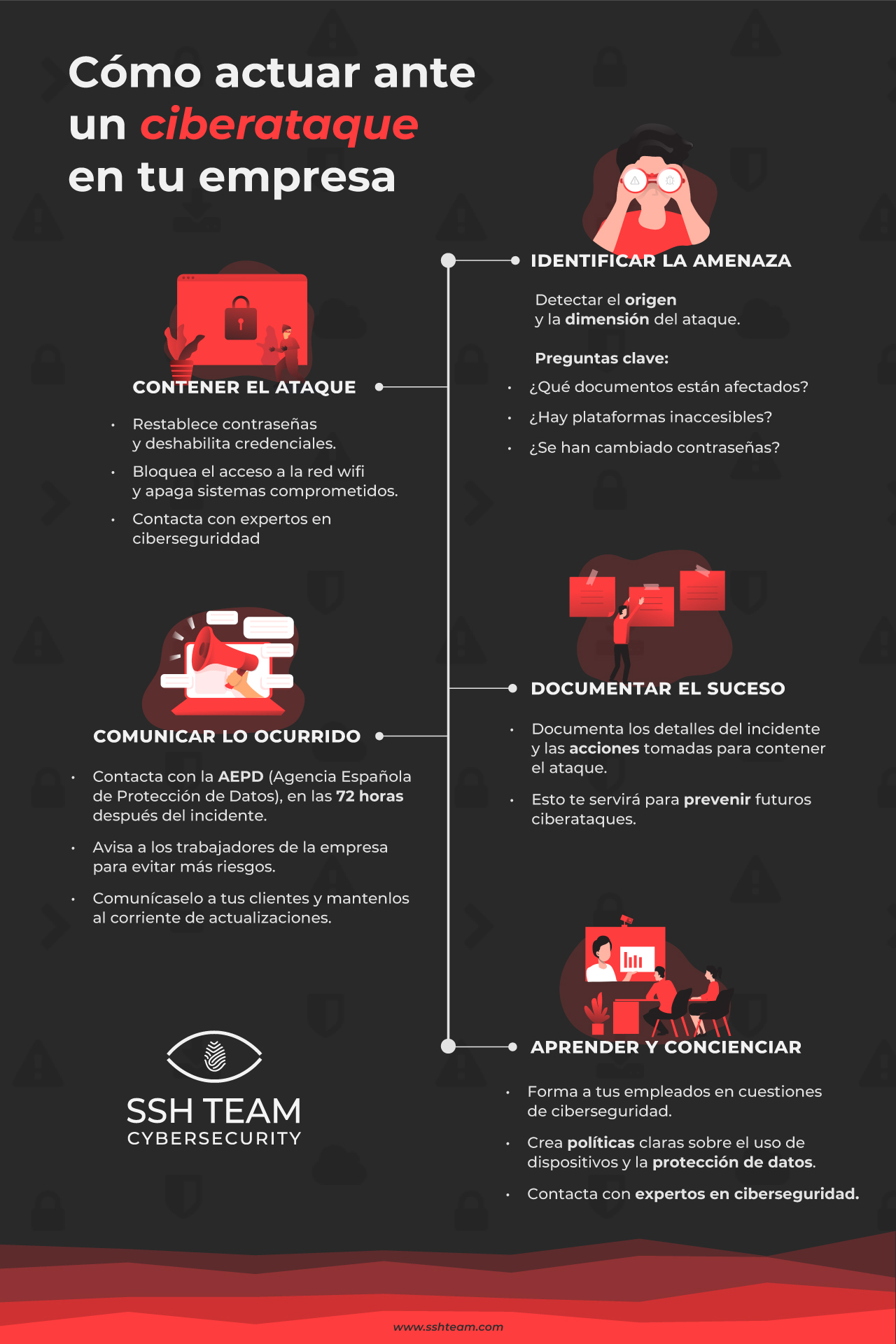
1. DETECTAR Y EVALUAR LAS AMENAZAS
En primer lugar, es crucial detectar el ciberataque cuanto antes, saber de dónde está viniendo y qué dimensión puede llegar a abarcar. Podemos hacerlo a través de un IDS, una herramienta para la detección de intrusiones y actividades sospechosas dentro de la red.
Preguntas clave para detectarlo:
- ¿Qué documentos están afectados?
- ¿Hay plataformas inaccesibles?
- ¿Se han cambiado contraseñas?
- ¿Se han instalado nuevas aplicaciones o servicios sin autorización?
- ¿Qué usuarios o cuentas muestran actividad sospechosa?
3. DOCUMENTAR EL SUCESO
Es esencial documentar todo lo que conocemos acerca de este suceso, de dónde viene la amenaza, cómo se ha detectado y quién, qué activos ha impactado y sobre todo, qué hemos hecho para contener el ataque.
Este documento nos puede servir para futuras incidencias y amenazas, así como para corregir las vulnerabilidades que han hecho posible el ataque. La documentación es un proceso continuo hasta que se cierra la actuación completa.
5. APRENDER Y CONCIENCIAR
Tras tener todo bajo control, debemos reflexionar sobre lo ocurrido y analizar la documentación elaborada para poder mejorarla y desarrollar un protocolo más efectivo para futuros ataques.
Además, siendo de especial importancia, concienciar y formar a los empleados en cuestiones de ciberseguridad.
2. CONTENER EL ATAQUE
Ahora que ya lo hemos identificado y sabemos dónde ubicarlo, hay que proceder a la contención de los elementos afectados. Esto nos ayuda a poder enfocarnos en la solución mientras evitamos que el ataque se propague a más activos.
Seguramente será necesario cambiar contraseñas y deshabilitar credenciales, bloquear el acceso a la red wifi y apagar todos los sistemas comprometidos. Y lo más importante, contactar con expertos en seguridad que nos puedan guiar en todo el proceso de recuperación.
4. COMUNICAR LO OCURRIDO
La transparencia es algo esencial para que la empresa mantenga la confianza de clientes y trabajadores, además, es de cumplimiento obligatorio comunicar a la Agencia de Protección de Datos que hemos sufrido un ciberataque, tenemos un margen de 72 h para hacérselo saber.
Por otro lado, debemos avisar tanto a los trabajadores de la empresa como a los clientes para que conozcan lo sucedido y las posibles amenazas que pueden enfrentar ellos como consecuencia, phishing, vishing y smishing entre otras.
Recursos adicionales
Si estás interesado en mejorar la seguridad de tu empresa y no sabes por dónde empezar, el INCIBE (Instituto Nacional de Ciberseguridad) proporciona guías enfocadas en el aprendizaje de los empresarios y recursos que facilitan la gestión de la ciberseguridad a las empresas.
AceleraPyme también tiene muchos recursos para empresas que pueden interesarte si quieres proteger tu negocio.
Si tienes curiosidad por la cantidad de ciberataques que se pueden dar, puedes acceder a este mapa en el que se visualiza, dónde y desde dónde, se están produciendo estos ciberataques en tiempo real.
¿Quieres comprobar la ciberseguridad de tu empresa?
Contacta con nosotros para realizar una auditoría de ciberseguridad. Si eres PyME, puedes acogerte a la subvención Activa Ciberseguridad




